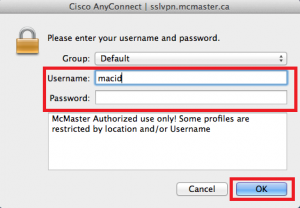
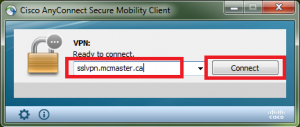
Connect to McMaster’s VPN using Cisco AnyConnect (executable’s location is /opt/cisco/anyconnect/bin/vpnui). See UTS VPN page ref 3 (#ref 3) for more information about connecting to the VPN Connect to virtual desktop using VMWare Horizon Client (executable’s location is /usr/local/bin/vmware-view).
Available - McMaster Virtual private network (VPN) is a technology that creates a safe and encrypted connection over the internet using a client from Cisco Systems called AnyConnect. The Cisco AnyConnect Secure Mobility Client for Apple iOS provides seamless and secure remote access to the McMaster Network. The client allows any installed application to communicate as though connected directly to McMaster. It is available from the iTunes App Store. All distribution and updates will be provided from the App Store. Cisco Anyconnect AnyConnect VPN server network from an off-campus, ezproxy, md, vpn, software allows you to gives remote users a sd for Scientists and - McMaster University The VPN on linux. Anyconnect GitHub Topics Administratively controlled policy.
Using openconnect
Install openconenct
openconnect sslvpn.mcmaster.ca(try with sudo if it fails)
If nothing failed, you should be connected
Tested on Xubuntu and Debian (x86_64).
Download the VPN client for linux, *.tar.gz fromhttps://www.mcmaster.ca/uts/network/vpn/
Download the VMWare Horizon client, *bundle fromhttps://www.vmware.com/go/viewclients
cd to the location of both downloads
Install libudev1 and libpangox-1.0-dev and if it is not already installed
Extract the VPN client
cd into the extracted directory
cd into the vpn directory
Install the VPN
cd back to directory where the files were downloaded to
Install VMWare Horizon client
Create a symlink [[notes 1]](#notes 1)
Connect to McMaster’s VPN using Cisco AnyConnect (executable’s location is/opt/cisco/anyconnect/bin/vpnui). See UTS VPN page[[ref 3]](#ref 3) for moreinformation about connecting to the VPN
Connect to virtual desktop using VMWare Horizon Client (executable’s location is/usr/local/bin/vmware-view). See CAS wiki page[[ref 1]](#ref 1) for more informationabout connecting to the virtual desktop
libudev.so.0is required for the Horizon client, butit appears that it is no longer available in the main repositories. Instead, for thepurposes of accessing the CAS Virtual Machines, symbolic linkinglibudev.so.1tolibudev.so.0works. [[ref 2]](#ref 2)
CAS Virtual Desktop wiki page
Ask Ubuntu answer regarding libudev.so.0
McMaster UTS VPN page
From Computing and Software Wiki
A Virtual Private Network (VPN) is used to create secure connections between hosts on the Internet. This is accomplished through tunneling and encryption. The advantage of a VPN is an inherent transparency of the service. This makes it valuable to different entities on the Internet, like corporations that want to provide secure connections to its employees.
How It Works
A VPN is possible because of two things. Tunneling and Encryption.1
- Tunneling:
Tunneling is the process of routing information of one protocol within another protocol. In VPN tunneling, the TCP/IP datagram with a virtual destination and source addresses is encapsulated in another TCP/IP datagram with actual addresses. When the datagram arrives at the location, the inner datagram is recovered and is delivered to its virtual address (which may not be on the same machine).
- Encryption:
Encryption is the act of reversibly altering data to make it unreadable to non-trusted users. In VPN, the VPN datagram is encrypted, so if it is intercepted, it will provide no information to the interceptor. But since it is encapsulated in another TCP/IP datagram it has no problem of reaching its destination.
What happens when information is sent through a VPN
McMaster University
1) The data is split into datagrams with the virtual VPN destination address and a virtual VPN source address.
2) The datagram is encrypted.
3) The encrypted mess of bits is placed into a TCP/IP datagram with actual source and destination addresses
4) The TCP/IP datagram is sent over the Internet to its destination.
5) If it arrives, the inner, encrypted datagram is recovered.
6) And decrypted.
7) And forwarded to its virtual VPN destination. The destination may be the same machine that received the TCP/IP datagram, or it may be a machine on the subnetwork.
History
At first, when two computers needed to be connected securely, a dedicated connection, in the shape of a direct cable, was established. This approach guaranteed that no information would be intercepted by placing the cable into difficult to reach places and by controlling access to it. The problem was that such a solution was only possible for short distances, laying a dedicated cable across a city (let alone a country) was extraordinary expensive.
On the other hand, during the end of the last century, there was a significant growth of the Internet. This enabled two computers virtually anywhere on Earth to be connected with a reliable and fast connection. On the other hand, the information traveling through the Internet could be easily intercepted. Because of this, there was a strive to create a virtual link through the physical network that would be protected from hampering with cryptography. This approach would be many times cheaper then creating a dedicated, physical link, and could be afforded by small companies.
When the idea caught on, it was extremely popular. Many IT corporations developed implementations of virtual private networks, not just in software but also on the hardware level. For example some of the companies that provided a VPN solution are:
- Cisco — L2F (LAYER 2 FORWARDING), L2TP (LAYER 2 TUNNELLING PROTOCOL), L2TPV3 (LAYER 2 TUNNELLING PROTOCOL VERSION 3)
- Microsoft — PPTP (POINT-TO-POINT TUNNELING PROTOCOL)
- Check Point Software Technologies — VPN-1
- Redcreek Communications — Ravlin
- Intel — LANROVER VPN EXPRESS
This creation of many different implementations implied that there was no standard for a VPN. Many implementations had security weaknesses, weak encoding techniques and no portability. Many implementations did not go beyond beta versions, but eventually, some grew into usable solutions, like OpenVPN. Primarly, VPN implementations were focused at delivering secure information from point to point. With time, they grew into more complicated networks, like extranet VPN, intranet VPN and remote access VPN. When more people started using VPNs, there was an effort to create and manage accounts with different levels of access. Then the support for different network protocols and eventually portability issues were raised.
Classifications 2
By type of medium:
- Protected:
Most popular type of VPNs. With these it is possible to create secure subnetworks based on a public network (Internet).These are: IPSec, OpenVPN and PPTP.
- Trusted:
Used in cases where a secure network is already provided and there is only a need for organizing a virtual subnetwork.These are: Multi-protocol label switching (MPLS) and L2TP (Layer 2 Tunnelling Protocol).
By implementation
- Hardware:
The VPN is implemented with a number of dedicated hardware devices. This allows for efficiency and usually security.
- Software:
The VPN is implemented as a software package.
- Integrated:
Functionality of the VPN is provided in a package of both hardware and software that also handles packet filtering, firewall and other network services.
Cisco Anyconnect Updates
By use
- Intranet VPN:
Used for creating a single protected network within a corporation between different physical locations using an unprotected, public network.
- Remote Access VPN:
Used for creating a private link between a segment of a corporation network and an employee that can connect to the company resources from a remote location.
- Extranet VPN:
Used for networks that allow 'semi-trusted' users (like clients) to connect to a company network. These users are not part of the corporation and so should have limited access to the company's resources.
By type of protocol
There are implementations of VPNs for TCP/IP, IPX and AppleTalk. But there is a general trend toward TCP/IP and practically every implementation supports TCP/IP.
By level of network protocol
There are implementations that can be attributed to different levels of the OSI models
McMaster
McMaster uses a VPN to let its students and staff to remotely connect and use the university resources. It can also be used to transfer files securely onto a university machine. For a student to connect to McMaster VPN they need to posses a MacID. McMaster recommends the use of a Cisco VPN client3, but other clients are also supported. Machines running Microsoft Windows are required to have up to date anti-virus software installed prior to connecting to the VPN.
Security
Most, but not all, VPN implementations use cryptography. Those that do include the following protocols:4
- IPsec (IP security)
- SSL/TLS
- OpenVPN
- L2TPv3 (Layer 2 Tunneling Protocol version 3)
- VPN Quarantine
- MPVPN
See Also
External Links
References
- [1] Internetworking with TCP/IP, fifth edition, Douglas E. Comer, 2006
- [2] VPN in Russian Wikipedia. Retrieved on 13-04-2008 http://ru.wikipedia.org/wiki/VPN
- [3] McMaster University VPN FAQ and installation guide. Retrieved on 13-04-2008 http://www.mcmaster.ca/uts/network/vpn
- [4] VPN in English Wikipedia. Retrieved on 13-04-2008 http://en.wikipedia.org/wiki/Vpn
- [5] Image 1 retrieved on 13-04-2008 http://www.checkpoint.com/products/vpn-1_clients/images/vpn-1_sc_connect.gif
--Pliassn 23:29, 13 April 2008 (EDT)
